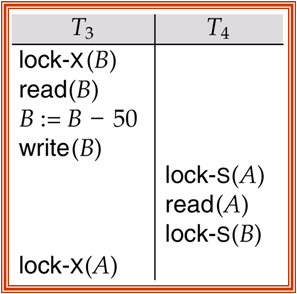
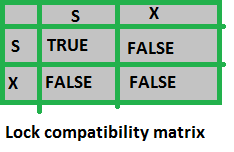
hardware raid vs software raid
A raid is considered hardware based when it is implemented in hardware. In software raid it just uses software instead of hardware. There are many difference between hardware and software raid. Describe below hardware raid vs software raid: 1. Cost : To implement hardware raid we need hardware disk but in software raid we just use software. So we can say that hardware raid costly than software raid. 2. Complexity : Software raid is a part of OS and it works on partition level. Sometimes software raid increases complexity but the complexity level of a hardware raid is low. 3. Performance : The performance of hardware raid always high but in software raid it depends upon use of the software. 4. Throughput : Hardware Raid offers higher throughput but software raid do not offers higher throughput. 5. Faster rebuilds : If any system failure occurs hardware raid recover it easily but it is not easy to rebuild software raid system. To improve this content plz make your comment.